Taking Control: Israeli cyber firm uncovers flaw that could have left 18 million Comcast remotes open to spying
According to GuardiCore, any hacker with a cheap RF transceiver could have used it to take over an XR11 remote; Comcast says it has patched up the vulnerability
16:0307.10.20
While security threats to home IoT (Internet of Things) devices have been widely researched over the last few years, one device that has gotten little attention as a potential attack vector, despite being one of the most common household items - the television remote. Tel Aviv-based cybersecurity startup GuardiCore Ltd. revealed on Wednesday that it discovered a security vulnerability on one of Comcast's widely-used voice-activated remote controllers that would have allowed attackers to turn it into a listening device.
Prior to its remediation by the American telecommunications conglomerate, the attack, dubbed WarezTheRemote, was a very real security threat. With more than 18 million units deployed across homes in the U.S, the XR11 is one of the most widespread remote controls in existence. WarezTheRemote used a man-in-the-middle attack to exploit the remote's RF communication. By extensively reverse-engineering both the remote’s firmware and the corresponding software it communicates with on the set-top box, GuardiCore was able to find a vulnerability in the way the remote handled incoming RF packets. As a result, attackers could have used the remote to continuously stream and record audio without user interaction. The attack did not require physical contact with the targeted remote or any interaction from the victim.
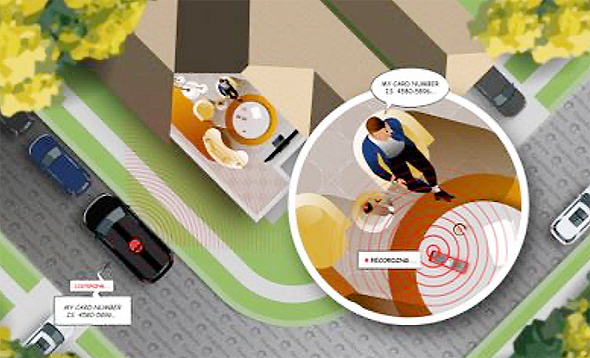
Israeli company GuardiCore revealed that a Comcast remote control was vulnerable to listening. Illustration: GuardiCoreהדמיה: גארדיקור
Comcast added in a statement: "Nothing is more important than keeping our customers safe and secure, and we appreciate Guardicore for bringing this issue to our attention. As detailed in this report, we fixed this issue for all affected Xfinity X1 Voice Remotes, which means the issue described here has been addressed and the attack exploiting it is not possible. Technologists for both Comcast and Guardicore confirmed that Comcast’s remediation not only prevents the attack described in this paper but also provides additional security against future attempts to deliver unsigned firmware to the X1 Voice Remote. Based on our thorough review of this issue, which included Guardicore’s research and our technology environment, we do not believe this issue was ever used against any Comcast customer."
GuardiCore reported the vulnerability to Comcast on April 21, with the telecom conglomerate beginning to look into the findings three days later. Comcast worked and released a patch during the summer and on September 24 confirmed all devices had been patched.

GuardiCore VP Security Ofri Ziv. Photo: Boris Kuznetzצילום: בוריס קוזנץ
"The set-top boxes were interesting to us due to the fact that they are directly connected to the telecommunication providers' server farms," said Ofri Ziv, VP Security at GuardiCore. "After breaking into the set-top we decided to take a look at the remote that came with it as well. The reason for our curiosity was that the remote comes with a microphone, which makes it an attractive target due to its listening capabilities. In addition, it supports RF communication which means you can communicate with it from long distances and even through walls."



